Sales Tax in Los Angeles County Just Went Up: Here’s What You Need to Know
Nina Gille Nielsen • April 7, 2025
Understanding LA County’s New Sales Tax Hike and What It Means for Your Business
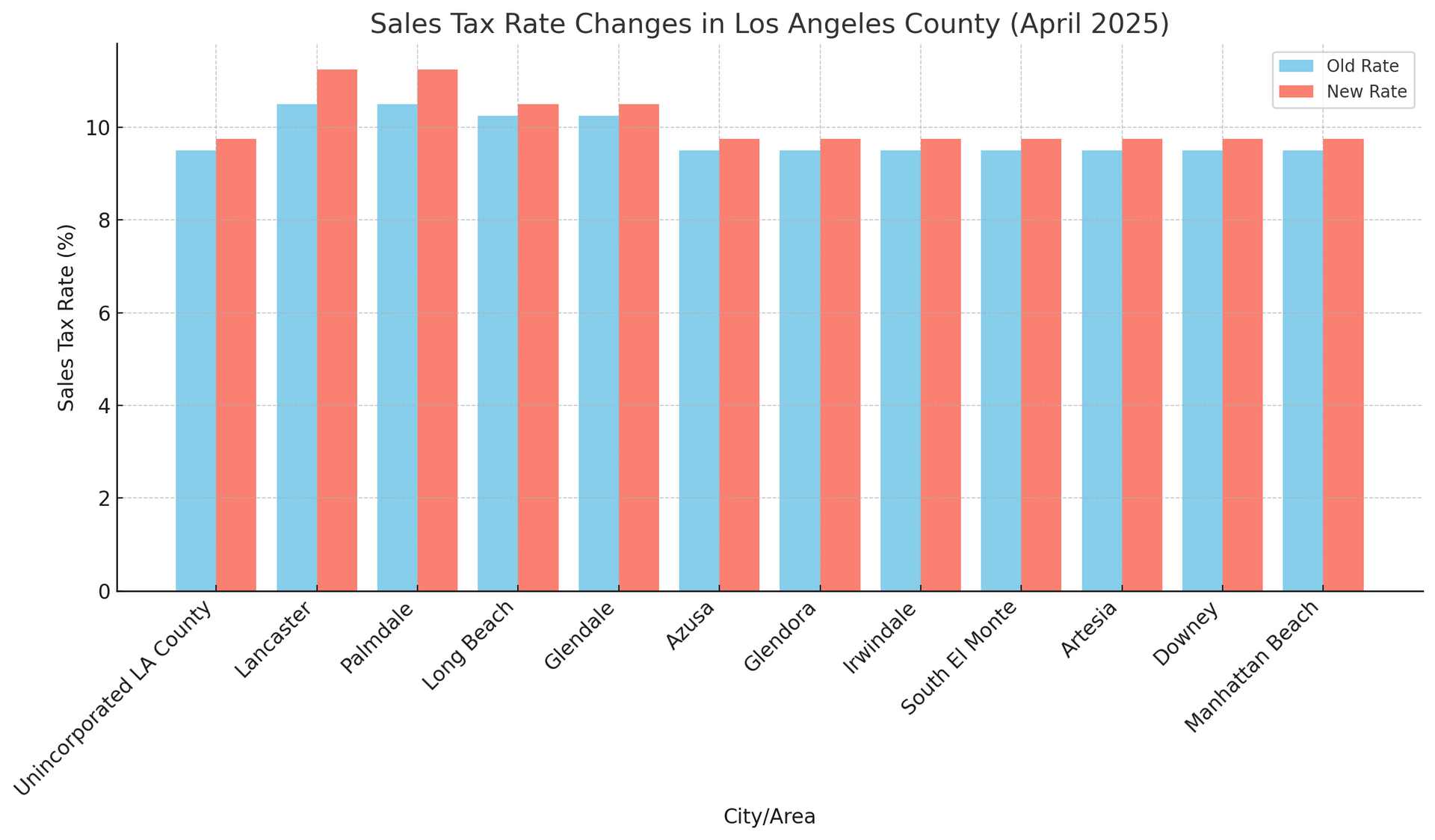
For some cities, the rise is even higher, raising questions, concerns, and necessary conversations about what this means for communities and local businesses. At Find Your Vision, we believe staying informed is the first step in adapting to change. So here’s a breakdown of what’s happening and why it matters.
What Is Measure A?
Measure A, officially known as the Los Angeles County Homelessness Services and Affordable Housing Ordinance, was passed by voters to address two of the most pressing issues in the region: homelessness and affordable housing.
The tax increase is expected to generate significant new funding for:
- Homeless services
- Affordable housing development
- Supportive programs for vulnerable populations
Unlike previous tax measures that had expiration dates, Measure A will remain in effect indefinitely, unless repealed by voters.
Where Is the Sales Tax Increasing, and By How Much?
Here’s a quick breakdown of how the new sales tax is affecting various areas:
Countywide (Most Areas)
- Old Rate: 9.5%
- New Rate: 9.75%
This increase affects unincorporated areas and cities that haven’t passed their own additional sales taxes.
Lancaster & Palmdale
- New Total Rate: 11.25%
- These cities approved their own 0.75% increase on top of Measure A, making them some of the highest in the county.
Long Beach & Glendale
- New Total Rate: 10.5%
- Up from 10.25% due to the countywide increase.
Cities Now Included Under Measure A
Cities that were previously excluded from Measure H, like Azusa, Glendora, Irwindale, South El Monte, Artesia, Downey, and Manhattan Beach, are now included under Measure A and will also see their sales tax rise to 9.75%.
What This Means for Local Businesses
For small businesses and entrepreneurs, particularly those operating in retail, hospitality, or service industries, this change may require:
- Revising pricing strategies
- Updating POS systems and accounting software
- Reassessing supply and customer engagement tactics
It also highlights the importance of staying connected to community needs. Businesses that support or align with the causes funded by Measure A may find ways to positively engage with their community while navigating these changes.
Stay Informed and Stay Compliant
According to the California Department of Tax and Fee Administration (CDTFA), the updated sales tax rates effective April 1, 2025, reflect a combination of statewide and voter-approved local measures, including Measure A in Los Angeles County. The CDTFA outlines that these rate changes apply to retail sales of tangible personal property and are enforceable across both incorporated and unincorporated areas. Businesses are required to update their point-of-sale systems and accounting practices to remain compliant with the new rates. You can find the full breakdown of updated rates and guidelines directly on the CDTFA’s official site.
A Note from Find Your Vision
As a nonprofit dedicated to uplifting entrepreneurs and underrepresented voices, we know that policy changes impact real people. That’s why we’re committed to keeping you informed, and ready, with the tools, context, and community you need to keep growing.
Have questions about how this sales tax increase may affect your business?
Let’s talk. We’re here to help you stay prepared and confident in the face of change.
Source:

If your desktop looks like a digital junk drawer and you can never find that one PDF when you need it, you are not alone. Digital clutter is a real problem, and it quietly costs time, focus, and peace of mind. The good news is that you do not need to be a tech expert to fix it. With a simple and consistent system, you can organize your files in a way that actually lasts. Below is a step-by-step approach to organizing your digital files so nothing important slips through the cracks again. Why File Organization Matters Disorganized digital spaces create unnecessary friction in daily work and personal life. Wasting just five minutes a day searching for files adds up to more than 20 hours per year Cluttered folders make backups less reliable and increase the risk of data loss Clean file systems reduce stress and help work feel more manageable Good organization is not about perfection. It is about clarity and consistency. Step 1: Create a Simple Folder Structure Avoid storing everything on your Desktop or in your Downloads folder. Instead, create a basic structure that mirrors how you think and work. Example structure:

Quantum computing is no longer confined to science fiction. With rapid advances by companies like IBM and Google, along with startups such as IonQ, the world is moving closer to practical quantum computers. These machines use quantum bits, or qubits, to process information in fundamentally new ways. One of the most profound implications of this technological leap is its potential to disrupt modern cryptography, the foundation of today’s digital security. What Is Quantum Computing? Unlike classical computers that use bits represented as either 0 or 1, quantum computers use qubits, which can exist in multiple states simultaneously through a phenomenon known as superposition. Combined with entanglement, this allows quantum systems to perform certain calculations exponentially faster than classical machines. This increased computational power enables quantum computers to solve problems that are currently considered infeasible, particularly those involving complex mathematical operations. Why Cryptography Is at Risk Modern cryptography relies on mathematical problems that are extremely difficult for classical computers to solve. Common encryption methods such as RSA and elliptic curve cryptography depend on the practical impossibility of factoring large numbers or solving discrete logarithm problems within a reasonable time frame. In 1994, mathematician Peter Shor introduced an algorithm that demonstrated how a sufficiently powerful quantum computer could efficiently factor large integers. If implemented at scale, Shor’s algorithm would undermine many of the cryptographic systems that secure today’s internet, financial transactions, and digital identities. What Could Be Broken by Quantum Computers? Once scalable and stable quantum computers exist, several widely used cryptographic algorithms could become vulnerable, including: RSA encryption Digital Signature Algorithm (DSA) Elliptic Curve Digital Signature Algorithm (ECDSA) Diffie-Hellman key exchange These algorithms underpin essential technologies such as secure web browsing (SSL/TLS), virtual private networks, secure email, blockchain authentication, and digital identity systems. When Will This Happen? Current quantum computers are not yet capable of breaking modern encryption. They lack the number of stable, error-corrected qubits required to perform large-scale cryptographic attacks. Experts estimate that breaking RSA-2048 encryption would require thousands of logical qubits and significant advances in quantum error correction. Predictions vary, but many researchers suggest that a practical quantum threat could emerge within the next 10 to 20 years. Some believe it could happen sooner, which is why preparation is already underway. The Shift Toward Post-Quantum Cryptography To address this looming risk, governments and organizations are developing post-quantum cryptography. These are cryptographic algorithms designed to remain secure against both classical and quantum attacks. In 2022, the National Institute of Standards and Technology announced its first set of standardized quantum-resistant algorithms. These include new approaches to public-key encryption and digital signatures that are intended to replace vulnerable legacy systems. What Organizations Should Do Now Preparation for a quantum future does not require waiting for quantum computers to fully mature. Organizations can take proactive steps today, including: Auditing systems to identify where classical cryptography is used Designing cryptographic agility into infrastructure so algorithms can be replaced without major disruption Testing post-quantum cryptographic algorithms in controlled environments Educating technical teams and leadership about quantum risks and mitigation strategies Early action reduces long-term risk and helps ensure continuity when cryptographic transitions become unavoidable. Quantum computing represents a fundamental shift in computing power, and cryptography may be one of the first areas to feel its impact. While the exact timeline remains uncertain, the threat is real enough that preparation is no longer optional. Organizations that begin transitioning toward quantum-resistant security today will be better positioned to protect data, maintain trust, and adapt to the next era of computing. In a quantum future, security will depend not on secrecy, but on resilience and foresight. Sources and Further Reading IBM Quantum Computing Overview https://www.ibm.com/quantum-computing Shor, P. W. (1994). Algorithms for Quantum Computation: Discrete Logarithms and Factoring https://ieeexplore.ieee.org/document/365700 National Institute of Standards and Technology (NIST), Post-Quantum Cryptography Project https://csrc.nist.gov/Projects/post-quantum-cryptography NIST (2022). Post-Quantum Cryptography Standardization Announcement https://www.nist.gov/news-events/news/2022/07/nist-announces-first-four-quantum-resistant-cryptographic RAND Corporation (2022). Is the Quantum Threat Real? https://www.rand.org/pubs/research_reports/RRA1025-1.html European Union Agency for Cybersecurity (ENISA). Post-Quantum Cryptography https://www.enisa.europa.eu/publications/post-quantum-cryptography

Find Your Vision (FYV)— We believe that young people already have powerful ideas, perspectives, and stories. Too often, they are simply missing the platform, access, or validation needed to share them. Today, we are proud to announce the launch of a new ongoing initiative: the FYV Youth Voices Blog Series. This blog series is designed to center young authors by giving them the opportunity to write about topics that matter to them. These pieces may explore culture, community, technology, social issues, creative expression, identity, sports, education, or any subject they feel compelled to examine. The goal is not to restrict voices, but to amplify them. Through this program, participating students will be able to earn internship or volunteer hours in partnership with their schools, while gaining real-world experience in writing, editing, publishing, and public-facing storytelling. Each published piece becomes a tangible work sample that students can reference on college applications, resumes, and scholarship materials. FYV will work directly with partnering schools to ensure this program aligns with their service-learning, internship, or volunteer hour requirements. Students will receive clear guidelines, mentorship where appropriate, and recognition for their contributions. Select pieces may also be featured across FYV’s digital platforms to further elevate student voices beyond the classroom. More than just a blog, Youth Voices is an opportunity for students to practice ownership of their ideas, develop confidence in their communication skills, and see their work taken seriously. Writing is not only a creative outlet; it is a tool for leadership, advocacy, and self-definition. We invite students, educators, counselors, and school administrators to join us in building this space together. If you are a young author with something to say, or a school interested in partnering with FYV to offer meaningful experiential learning opportunities, we welcome you. This is only the beginning. Your voice matters. And we’re here to help you share it. Students interested in participating in the FYV Youth Voices Blog Series may enter through a partnering school, sponsored program, or one of FYV’s active initiatives. For individuals who are not currently part of a partnered school or FYV-sponsored program, submissions and inquiries are still welcome. Independent students, young writers, or families may reach out directly to us at nina@findyourvision.org for submission guidelines, eligibility details, and information on how published work may qualify for volunteer or experiential learning hours.

In today’s hyperconnected world, the traditional model of funneling all data to centralized cloud servers is showing its limitations. As real-time processing and latency-sensitive applications become the norm, edge computing has emerged as a critical evolution in IT infrastructure. What Is Edge Computing? Edge computing is a distributed computing model that brings computation and data storage closer to the physical location where it’s needed, whether that’s a factory floor, retail store, or autonomous vehicle. Instead of sending data to the cloud for processing, edge devices handle tasks locally or near the source of data generation. This reduces latency, saves bandwidth, and improves response times. Source: IBM. What is edge computing? Why It Matters Now 1. Demand for Low Latency - Applications like autonomous vehicles, augmented reality, and industrial automation require near-instantaneous processing. Every millisecond counts. 2. Explosion of IoT Devices - With billions of IoT devices expected to come online, sending all data to the cloud would overwhelm networks and data centers. Source: Statista (2024), Number of IoT Devices Worldwide 2020–2030 3. Bandwidth and Cost Optimization - Processing data at the edge minimizes the need to send massive amounts of information over the internet, cutting down bandwidth costs and latency. How Edge Changes Network Architecture Distributed Infrastructure Networks are evolving from a centralized hub-and-spoke model to a distributed mesh where compute nodes are located at or near data sources. Local Data Processing Edge nodes filter, analyze, and act on data in real time before forwarding only essential information to centralized systems. Micro Data Centers Edge environments use compact data centers, often deployed in remote or mobile locations such as 5G towers, retail kiosks, or vehicles. Source: Intel, Edge Computing and Network Transformation Key Use Cases Autonomous Vehicles Edge computing enables real-time decision-making for navigation, safety, and object detection without waiting for cloud processing. Smart Manufacturing Factories use edge devices to control machines, detect anomalies, and adjust operations instantly to optimize production. Remote Healthcare Edge systems in medical devices allow for real-time patient monitoring and analytics, crucial in emergency care or remote locations. Source: McKinsey & Company, What’s Next for the Industrial Edge? Benefits of Edge Computing Ultra-Low Latency: Ideal for real-time processing Enhanced Data Privacy: Sensitive data stays local Reduced Network Load: Only essential data is sent to the cloud Improved Reliability: Systems can continue operating even if internet connectivity is lost Challenges to Adoption Infrastructure Investment: Requires hardware at the edge and integration with existing systems Security Risks: More distributed nodes mean a larger attack surface Skilled Talent: Edge environments require expertise in networking, AI, and embedded systems Source: Gartner, Emerging Technologies: Edge Computing Edge computing is a foundational shift in IT strategy. As technologies like 5G, AI, and IoT continue to mature, edge computing will serve as the glue that binds them together. By processing data where it’s created and needed most, organizations can enable smarter services, reduce costs, and unlock new digital possibilities. Sources: IBM. What is edge computing? Statista. Number of IoT devices worldwide 2020–2030 Intel. Edge Computing and Network Transformation McKinsey & Company. What’s next for the Industrial Edge? Gartner. Emerging Technologies: Edge Computing

If you use Google Calendar only to keep track of meetings, you are missing out on some seriously helpful features. Google Calendar can do more than remind you what is next. It can help you get more done, stay organized, and save hours every week. Below are five practical, time saving Google Calendar tricks you can start using right now. 1. Use Appointment Slots to Let People Book Time With You What it does: Allows others to schedule meetings with you directly based on your availability. Perfect for: Teachers, freelancers, managers, or anyone tired of back and forth emails asking when you are free. How to use it: Open Google Calendar. Click anywhere on your calendar and select Appointment schedule. Set your available time slots and share the booking link. Source: Google Workspace Learning Center, Appointment Schedules https://support.google.com/calendar/answer/10729749 2. Color Code Events to Stay Focused What it does: Assigns colors to different types of events, such as meetings, personal time, or deep work. Why it saves time: You can instantly see how your time is being used and adjust your schedule more intentionally. How to use it: Right click an event and choose a color. Use consistent colors across your calendar for clarity. Source: Google Calendar Help, Change Event Color https://support.google.com/calendar/answer/6084644 3. Set Recurring Events Instead of Re Entering Tasks What it does: Automatically repeats events daily, weekly, or monthly. Perfect for: Team meetings, bill reminders, workouts, or weekly routines. How to use it: When creating an event, select Does not repeat and choose how often it should repeat. You can also add custom rules or end dates. Source: Google Calendar Help, Create Recurring Events https://support.google.com/calendar/answer/37115 4. Receive a Daily Agenda by Email What it does: Sends a summary of your schedule to your inbox every morning. Why it saves time: You can see your day at a glance without opening your calendar. How to use it: Open Google Calendar on desktop. Click the gear icon and select Settings. Choose your calendar under Settings for my calendars. Scroll to Other notifications and enable Daily agenda. Source: Google Calendar Notifications Help https://support.google.com/calendar/answer/37242 5. Sync Work and Personal Calendars in One View What it does: Combines multiple calendars so you do not double book or miss events. Perfect for: Anyone managing personal, work, or school schedules. How to use it: Under Other calendars, click the plus icon and subscribe to another calendar or add one via URL. You can also connect Outlook or Apple calendars with additional setup. Source: Google Calendar Help, Add or Subscribe to Calendars https://support.google.com/calendar/answer/37100 Bonus Tip: Enable Keyboard Shortcuts Use shortcuts like C to create a new event or D to switch to Day view. Turn them on in Settings by enabling keyboard shortcuts. Source: Google Calendar Keyboard Shortcuts https://support.google.com/calendar/answer/181586 Google Calendar is not just a scheduling tool. It is a productivity assistant hiding in plain sight. A few small tweaks can save you time every single day. Color code your calendar, automate recurring tasks, and let your schedule work for you instead of against you. If you want, I can also format this for LinkedIn, turn it into a carousel graphic, or create a short caption to go with it. Sources Google Workspace Learning Center, Appointment Schedules https://support.google.com/calendar/answer/11608416 Google Calendar Help, Change Event Colors https://support.google.com/calendar/answer/6084644 Google Calendar Help, Create Recurring Events https://support.google.com/calendar/answer/37115 Google Calendar Help, Notifications and Daily Agenda https://support.google.com/calendar/answer/37242 Google Calendar Help, Add or Subscribe to Calendars https://support.google.com/calendar/answer/37100 Google Calendar Keyboard Shortcuts https://support.google.com/calendar/answer/37113

Let’s face it, life is already complicated. Your tech tools should make it easier, not harder. From automating boring tasks to organizing your day quickly, here are six free or low cost tools that anyone can use to simplify their digital life, even if you are not tech savvy. 1. Todoist Organize Your Tasks and Clear Your Mind What it does: Todoist is a simple to do list app that works across all devices. Use it to: Jot down ideas Set daily reminders Create recurring tasks like paying bills on the first of each month You can also tag tasks such as work or home and share lists with family members or coworkers. Source: Todoist Features Overview 2. Zapier Automate Repetitive Tasks What it does: Zapier connects apps so you do not have to repeat the same tasks manually. Examples include: Automatically saving Gmail attachments to Google Drive Adding Zoom meeting links to Google Calendar Receiving a Slack message when someone fills out a form It works like a personal assistant and is free for up to one hundred tasks per month. Source: Zapier Starter Guide 3. Clean Email Declutter Your Inbox Quickly What it does: Clean Email helps you unsubscribe in bulk, block senders, and automatically delete old emails. It is useful for: Reducing stress caused by inbox overload Creating rules like deleting newsletters older than seven days It works with Gmail, Outlook, Yahoo, and other email providers. Source: Clean Email How It Works 4. Bitwarden Remember One Password Instead of Dozens What it does: Bitwarden is a password manager that securely stores your logins. With Bitwarden you can: Store passwords, secure notes, and payment information Autofill login forms Sync data securely across devices It is open source, free to use, and fully encrypted. Source: Bitwarden Security Overview 5. Notion Your All in One Digital Workspace What it does: Notion combines notes, task lists, documents, and databases in one place. You can use it to: Track projects Keep journals Plan trips Share documents with a team It may look overwhelming at first, but using templates makes it easy to get started. Source: Notion Beginner’s Guide 6. Google Calendar Take Control of Your Time What it does: Google Calendar helps you manage meetings, reminders, and recurring events. Helpful features include: Custom alerts such as ten minutes or one day before an event Color coding for different types of activities Calendar sharing with family or coworkers It works especially well when paired with tools like Zapier or Todoist. Source: Google Calendar Tips You do not need to be a tech expert to live a more organized and productive life. A few easy tools used intentionally can save hours each week, reduce stress, and help you feel more in control. Most of these tools are free to start. Try one at a time and build from there. Sources: Todoist Features Overview https://todoist.com/features Zapier Getting Started and Automation Examples https://zapier.com/learn/getting-started-guide/ Clean Email How Clean Email Works https://clean.email/how-it-works Bitwarden Security and Encryption Overview https://bitwarden.com/security/ Notion Beginner’s Guide https://www.notion.so/help/guides/notion-for-beginners Google Calendar Tips and Productivity Features https://support.google.com/calendar/answer/37111

Cryptocurrency has revolutionized the way we think about money and investments. But with innovation comes risk, and in the crypto space, scams are alarmingly common. From phishing schemes to fake investment platforms, crypto scams have cost investors billions globally. If you are trading, investing, or even just curious about crypto, it is crucial to know how to protect yourself. Common Types of Crypto Scams 1. Phishing Scams Scammers often pose as crypto exchanges or wallet providers, sending emails or direct messages asking for login credentials or seed phrases. These messages look official but are designed to steal your information. Red flag : Unexpected messages asking you to verify your wallet or secure your account. 2. Fake Investment Platforms Some websites promise high returns with little or no risk. Once you deposit funds, they may display fake gains, but you will never be able to withdraw your money. Red flag : Guaranteed returns or promises to double your Bitcoin overnight. 3. Giveaway Scams Common on social media, scammers impersonate celebrities or influencers, often Elon Musk, claiming to give away cryptocurrency. To receive the gift, you are instructed to send crypto first. Red flag : Any giveaway that asks for crypto upfront. 4. Rug Pulls This occurs when developers launch a crypto project or token, attract investors, then suddenly disappear with the funds. These scams are especially common in decentralized finance and meme coins. Red flag : A brand-new project with anonymous developers and no roadmap or audit. 5. Ponzi and Pyramid Schemes These schemes revolve around recruiting others to invest, with returns paid using money from new participants rather than actual profits. Eventually, the system collapses. Red flag : Heavy emphasis on referrals and recruiting instead of the actual product or service. How to Protect Yourself Use reputable platforms. Stick to well-known exchanges such as Coinbase, Binance, or Kraken, and always double-check the website URL, as phishing sites often mimic real ones. Enable two-factor authentication. Additional security layers make it much harder for attackers to access your wallet. Never share your seed phrase. Your recovery phrase is the master key to your crypto wallet, and no legitimate service will ever request it. Do your own research. Before investing in any token or project, read whitepapers, research the team, and review community feedback. If something feels off, it probably is. Be skeptical of hype. Scams often rely on fear of missing out tactics. Avoid rushing into investments based on social media trends or promises of quick riches. While the crypto world is exciting, it also attracts fraudsters. Awareness is your strongest defense. If a deal sounds too good to be true, it usually is. By staying informed and cautious, you can explore cryptocurrency responsibly and reduce the risk of falling victim to scams. Sources: Federal Trade Commission (FTC) — “Cryptocurrency Scams” page: https://www.ftc.gov/media/cryptocurrency-scams Chainalysis — “2025 Crypto Crime Report”: https://go.chainalysis.com/2025-Crypto-Crime-Report.html Investopedia — “Beware These Five Bitcoin Scams” (crypto scam guide): https://www.investopedia.com/articles/forex/042315/beware-these-five-bitcoin-scams.asp



